Hallo Liebe Community ich hoffe mir kann Jemand helfen,
Router ist der Port 1194 offen für die NAS
ich habe folgendes Problem ich bekomme bi der Verbindung zu der OPENVPN folgende fehler im Client angezeigt
Fehler
TLS Error: local/remote TLS keys are out of sync: [AF_INET]XXXXXXXXXX [0]
Warnings
--cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-f
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1585', remote='link-mtu 1601'
WARNING: 'keysize' is used inconsistently, local='keysize 128', remote='keysize 256
WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
hier die Client Setting
dev tun
tls-client
remote xxxxxxxxxxxx 1194
# The "float" tells OpenVPN to accept authenticated packets from any address,
# not only the address which was specified in the --remote option.
# This is useful when you are connecting to a peer which holds a dynamic address
# such as a dial-in user or DHCP client.
# (Please refer to the manual of OpenVPN for more information.)
#float
# If redirect-gateway is enabled, the client will redirect it's
# default network gateway through the VPN.
# It means the VPN connection will firstly connect to the VPN Server
# and then to the internet.
# (Please refer to the manual of OpenVPN for more information.)
#redirect-gateway def1
# dhcp-option DNS: To set primary domain name server address.
# Repeat this option to set secondary DNS server addresses.
#dhcp-option DNS DNS_IP_ADDRESS
pull
# If you want to connect by Server's IPv6 address, you should use
# "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode
tun-mtu 1500
proto udp
script-security 2
reneg-sec 0
data-ciphers AES-256-CBC
auth SHA512
auth-user-pass
<ca>
-----BEGIN CERTIFICATE-----
XXXXXXXX
-----END CERTIFICATE-----
</ca>
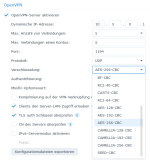
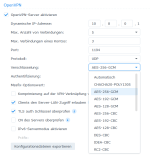
SERVER Config
Port 1194
Protokoll UDP
Verschlüsselung AES-256-CBC
Authentifizierung SHA512
Mssfix 1450
Komprimierung auf der VPN: kein Haken
Clients den Server Lang Zugriff erlauben: Haken gesetzt
NAS ist eine 415+
Router ist der Port 1194 offen für die NAS
ich habe folgendes Problem ich bekomme bi der Verbindung zu der OPENVPN folgende fehler im Client angezeigt
Fehler
TLS Error: local/remote TLS keys are out of sync: [AF_INET]XXXXXXXXXX [0]
Warnings
--cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-f
WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1585', remote='link-mtu 1601'
WARNING: 'keysize' is used inconsistently, local='keysize 128', remote='keysize 256
WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
hier die Client Setting
dev tun
tls-client
remote xxxxxxxxxxxx 1194
# The "float" tells OpenVPN to accept authenticated packets from any address,
# not only the address which was specified in the --remote option.
# This is useful when you are connecting to a peer which holds a dynamic address
# such as a dial-in user or DHCP client.
# (Please refer to the manual of OpenVPN for more information.)
#float
# If redirect-gateway is enabled, the client will redirect it's
# default network gateway through the VPN.
# It means the VPN connection will firstly connect to the VPN Server
# and then to the internet.
# (Please refer to the manual of OpenVPN for more information.)
#redirect-gateway def1
# dhcp-option DNS: To set primary domain name server address.
# Repeat this option to set secondary DNS server addresses.
#dhcp-option DNS DNS_IP_ADDRESS
pull
# If you want to connect by Server's IPv6 address, you should use
# "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode
tun-mtu 1500
proto udp
script-security 2
reneg-sec 0
data-ciphers AES-256-CBC
auth SHA512
auth-user-pass
<ca>
-----BEGIN CERTIFICATE-----
XXXXXXXX
-----END CERTIFICATE-----
</ca>
SERVER Config
Port 1194
Protokoll UDP
Verschlüsselung AES-256-CBC
Authentifizierung SHA512
Mssfix 1450
Komprimierung auf der VPN: kein Haken
Clients den Server Lang Zugriff erlauben: Haken gesetzt
NAS ist eine 415+