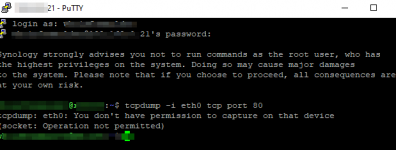
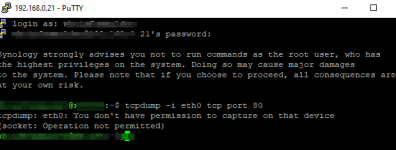
root@xfiles:~# tcpdump -n -i eth0 port 80
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
13:45:28.781238 IP 98.44.67.79.80 > 192.168.0.21.49200: Flags [SE], seq 0, win 65453, length 0
13:45:28.781323 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0
13:45:29.780698 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0
13:45:31.780701 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0
13:45:35.780700 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0
13:45:43.780699 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0
13:45:59.780698 IP 192.168.0.21.49200 > 98.44.67.79.80: Flags [S.], seq 3176416477, ack 1, win 29200, options [mss 1460], length 0