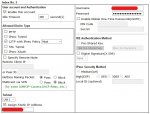
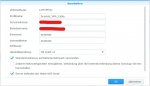
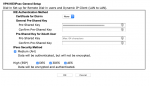
Hallo,
vielen Dank für Deine Hilfe und Tips!
Ich habe beides ausprobiert. Sowohl den IPsec-Tunnel an/ausgeschaltet und bei L2TP auf "nice to have" und auch "none". Beides hat leider nicht zum Erfolg geführt. Die Anfrage kommt definitiv beim Router an, die werden sich aber irgendwie nicht einig.
Während eines Verbindungs-Versuchs habe ich auf beiden Seiten das Log mitgeschrieben. Weiß einer von Euch, woran die Verbindung scheitert? Meine Kenntnisse reichen dafür nicht aus:
Log der DS218 (Leserichtung von oben nach unten)
----------------------
2019-03-26T19:29:13+01:00 DS218play gateway_change hook event: NEW 0.0.0.0 on eth0
2019-03-26T19:29:13+01:00 DS218play ipsec_setup: Starting Openswan IPsec U2.6.46/K4.4.59+...
2019-03-26T19:29:13+01:00 DS218play ipsec_setup: Using NETKEY(XFRM) stack
2019-03-26T19:29:14+01:00 DS218play ipsec_setup: ...Openswan IPsec started
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: adjusting ipsec.d to /etc/ipsec.d
2019-03-26T19:29:14+01:00 DS218play pluto: adjusting ipsec.d to /etc/ipsec.d
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: Labelled IPsec not enabled; value 32001 ignored.
2019-03-26T19:29:14+01:00 DS218play pluto: Labelled IPsec not enabled; value 32001 ignored.
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding connection: "L2TP-PSK-CLIENT"
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 listening for IKE messages
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding interface eth0/eth0 192.168.1.10:500
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding interface eth0/eth0 192.168.1.10:4500
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding interface lo/lo 127.0.0.1:500
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding interface lo/lo 127.0.0.1:4500
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 adding interface lo/lo ::1:500
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 loading secrets from "/etc/ipsec.secrets"
2019-03-26T19:29:14+01:00 DS218play ipsec__plutorun: 002 SYNO: IPSEC ready.
2019-03-26T19:29:53+01:00 DS218play synovpnc: connection.c:768 Wait 30 seconds; Failed to get net card info '' [0x0900 file_get_line.c:25]
2019-03-26T19:29:53+01:00 DS218play synovpnc: connection.c:866 /usr/syno/etc.defaults/synovpnclient/scripts/l2tpc.sh failed
2019-03-26T19:29:54+01:00 DS218play gateway_change hook event: DEL 0.0.0.0 on eth0
2019-03-26T19:29:55+01:00 DS218play ipsec_setup: Stopping Openswan IPsec...
2019-03-26T19:29:55+01:00 DS218play ipsec_setup: rmmod: ERROR: Module xfrm4_mode_transport is in use
2019-03-26T19:29:55+01:00 DS218play ipsec_setup: rmmod: ERROR: Module esp4 is in use
2019-03-26T19:29:58+01:00 DS218play ipsec_setup: ...Openswan IPsec stopped
2019-03-26T19:29:58+01:00 DS218play xl2tpd[32510]: death_handler: Fatal signal 15 received
2019-03-26T19:29:59+01:00 DS218play synovpnc: connection.c:1296 CreateL2TPConnection(l1553596455) failed
2019-03-26T19:29:59+01:00 DS218play synovpnc: synovpnc.c:376 VPN id 'l1553596455' is failed to create
Log des Draytek-Routers (Leserichtung von unten nach oben)
----------------------
"2019-03-26 19:29:18", "[L2TP][@192.168.1.10] IKE release: state wait_L2"
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:12, Tunnel ID:10, Session ID:0, Ns:4, Nr:4"
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:12, Tunnel ID:10, Session ID:8, Ns:4, Nr:3"
"2019-03-26 19:29:17", "L2TP ==> Control(0xC802)-L-S Ver:2 Len:38, Tunnel ID:22612, Session ID:0, Ns:3, Nr:4"
"2019-03-26 19:29:17", "L2TP ==> Control(0xC802)-L-S Ver:2 Len:38, Tunnel ID:22612, Session ID:35961, Ns:2, Nr:4"
"2019-03-26 19:29:17", "[L2TP][@192.168.1.10] pppShutdown "
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:50, Tunnel ID:10, Session ID:8, Ns:3, Nr:2"
"2019-03-26 19:29:17", "L2TP ==> Control(0xC802)-L-S Ver:2 Len:28, Tunnel ID:22612, Session ID:35961, Ns:1, Nr:3"
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:48, Tunnel ID:10, Session ID:0, Ns:2, Nr:1"
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:20, Tunnel ID:10, Session ID:0, Ns:1, Nr:1"
"2019-03-26 19:29:17", "L2TP ==> Control(0xC802)-L-S Ver:2 Len:104, Tunnel ID:22612, Session ID:0, Ns:0, Nr:1"
"2019-03-26 19:29:17", "L2TP <== Control(0xC802)-L-S Ver:2 Len:106, Tunnel ID:0, Session ID:0, Ns:0, Nr:0"
"2019-03-26 19:29:14", "IPsec SA established with 192.168.1.10. In/Out Index: 66/0"
"2019-03-26 19:29:14", "IPsec SA #9 will be replaced after 23925 seconds"
"2019-03-26 19:29:14", "IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x68f27541"
"2019-03-26 19:29:14", "IKE ==>, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x68f27541"
"2019-03-26 19:29:14", "Responding to Quick Mode from 192.168.1.10"
"2019-03-26 19:29:14", "[IPSEC/IKE][Local][66:-][@192.168.1.10] quick_inI1_outR1: match network"
"2019-03-26 19:29:14", "Receive client L2L remote network setting is 192.168.1.2/32"
"2019-03-26 19:29:14", "Accept ESP prorosal ENCR ESP_AES, HASH AUTH_ALGORITHM_HMAC_SHA1 "
"2019-03-26 19:29:14", "IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x20, Message ID = 0x68f27541"
"2019-03-26 19:29:14", "sent MR3, ISAKMP SA established with 192.168.1.10. In/Out Index: 66/0"
"2019-03-26 19:29:14", "IKE ==>, Next Payload=ISAKMP_NEXT_ID, Exchange Type = 0x2, Message ID = 0x0"
"2019-03-26 19:29:14", "IKE <==, Next Payload=ISAKMP_NEXT_ID, Exchange Type = 0x2, Message ID = 0x0"
"2019-03-26 19:29:14", "IKE ==>, Next Payload=ISAKMP_NEXT_KE, Exchange Type = 0x2, Message ID = 0x0"
"2019-03-26 19:29:14", "Matching General Setup key for dynamic ip client..."
"2019-03-26 19:29:14", "NAT-Traversal: Using RFC 3947, no NAT detected"
"2019-03-26 19:29:14", "IKE <==, Next Payload=ISAKMP_NEXT_KE, Exchange Type = 0x2, Message ID = 0x0"
"2019-03-26 19:29:14", "IKE ==>, Next Payload=ISAKMP_NEXT_SA, Exchange Type = 0x2, Message ID = 0x0"
"2019-03-26 19:29:14", "Accept Phase1 prorosals : ENCR OAKLEY_AES_CBC, HASH OAKLEY_SHA "
"2019-03-26 19:29:14", "Matching General Setup key for dynamic ip client..."
"2019-03-26 19:29:14", "Responding to Main Mode from 192.168.1.10"
"2019-03-26 19:29:14", "IKE <==, Next Payload=ISAKMP_NEXT_SA, Exchange Type = 0x2, Message ID = 0x0"
Andere Geräte können problemlos eine VPN-Verbindung herstellen.
Vielen Dank für Eure Hilfe,
SHC