#-------------------------------------------------------------------------------
# Pi.Alert
# Open Source Network Guard / WIFI & LAN intrusion detector
#
# pialert.conf - Back module. Configuration file
#-------------------------------------------------------------------------------
# Puche 2021 pi.alert.application@gmail.com GNU GPLv3
#-------------------------------------------------------------------------------
PIALERT_PATH = '/home/egal/pialert'
DB_PATH = PIALERT_PATH + '/db/pialert.db'
LOG_PATH = PIALERT_PATH + '/log'
VENDORS_DB = '/usr/share/arp-scan/ieee-oui.txt'
PRINT_LOG = False
SMTP_SERVER = 'smtp.gmail.com'
SMTP_PORT = 587
SMTP_USER = 'egal@gmail.com'
SMTP_PASS = 'egal'
REPORT_MAIL = False
REPORT_FROM = 'Pi.Alert <' + SMTP_USER +'>'
REPORT_TO = 'egal@gmail.com'
REPORT_DEVICE_URL = 'http://pi.alert/deviceDetails.php?mac='
# QUERY_MYIP_SERVER = 'https://diagnostic.opendns.com/myip'
QUERY_MYIP_SERVER = 'http://ipv4.icanhazip.com'
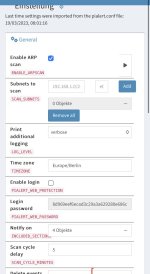
DDNS_ACTIVE = False
DDNS_DOMAIN = 'your_domain.freeddns.org'
DDNS_USER = 'dynu_user'
DDNS_PASSWORD = 'A0000000B0000000C0000000D0000000'
DDNS_UPDATE_URL = 'https://api.dynu.com/nic/update?'
PIHOLE_ACTIVE = True
PIHOLE_DB = '/etc/pihole/pihole-FTL.db'
DHCP_ACTIVE = False
DHCP_LEASES = '/etc/pihole/dhcp.leases'
# arp-scan options & samples
#
# Scan local network (default)
# SCAN_SUBNETS = '--localnet'
#
# Scan two subnets
# SCAN_SUBNETS = '192.168.11.0/24 192.168.144.0/24'
#
# Scan using interface eth0
# SCAN_SUBNETS = '--localnet --interface=eth0'
SCAN_SUBNETS = '--localnet'